TRACE CABLES THE EASY WAY WITH CISCO CDP ON WINDOWS
Download tool from:
https://www.definit.co.uk/2010/02/trace-cables-the-easy-way-with-cisco-cdp-on-windows/
Example of usage:
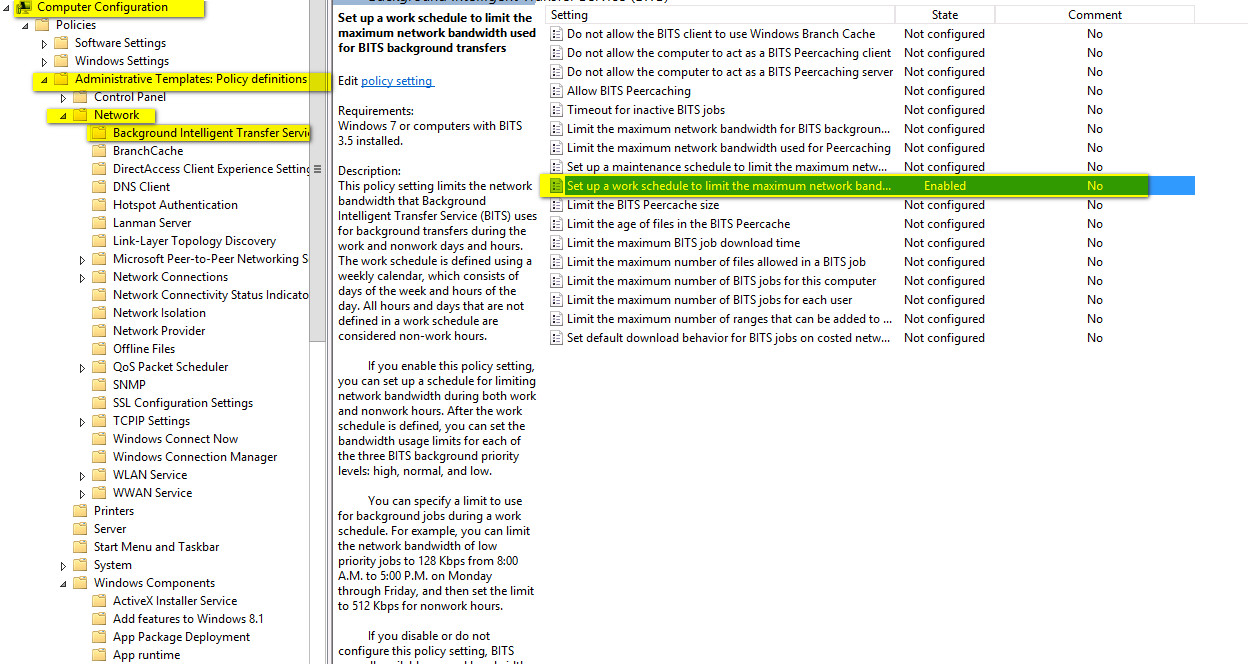
Step1:
c:\temp\tcpdumptcpdump.exe -D
********************************************************************
** **
** Tcpdump v4.9.2 (September 03, 2017) **
** http://www.tcpdump.org **
** **
** Tcpdump for Windows is built with Microolap Packet Sniffer SDK **
** Microolap EtherSensor product family **
** build 5072.01 June 10, 2019 <<< **
** **
** Copyright(c) 1997 - 2019 Microolap Technologies **
** http://microolap.com/products/network/ethersensor **
** http://microolap.com/products/network/tcpdump **
** **
** XP/2003/Vista/2008/Win7/Win8 **
** Win2012/Win10/Win2016/Win2019 **
** (UEFI and Secure Boot compatible) **
** **
** Trial license. **
** **
********************************************************************
1.\Device\{F4F682D0-3FEA-4DF1-9385-878235FC4177} (Intel(R) I350 Gigabit Network Connection)
2.\Device\{FF4C946F-ADB3-4DC9-A61A-A91973AFD7E8} (Intel(R) I350 Gigabit Network Connection)
3.\Device\{6C48897F-B39D-4298-B3D3-19402E588D0E} (Intel(R) I350 Gigabit Network Connection)
4.\Device\{D6A49332-2416-4227-89F5-55A5AA19578F} (Intel(R) Ethernet Converged Network Adapter X710)
5.\Device\{7C3220F8-224E-4867-B050-E252D849E404} (Intel(R) Ethernet Converged Network Adapter X710-2)
6.\Device\{9A86189E-CD60-4FD6-93C5-64E8DF14337D} (Intel(R) Ethernet Converged Network Adapter X710-2)
7.\Device\{32BBADAE-BA53-433C-B796-C51CC9526F23} (Intel(R) I350 Gigabit Network Connection)
8.\Device\{B87C05E6-1BF1-4126-AF7C-E01BC0D507DD} (Intel(R) Ethernet Controller X540-AT2)
9.\Device\{543DFBD5-610B-4165-B9B2-B1C6447272C7} (Intel(R) Ethernet Converged Network Adapter X710)
10.\Device\{CB9851A4-A64A-4F31-8AF8-97A812217C44} (Intel(R) Ethernet Controller X540-AT2)
which of interfaces is our?
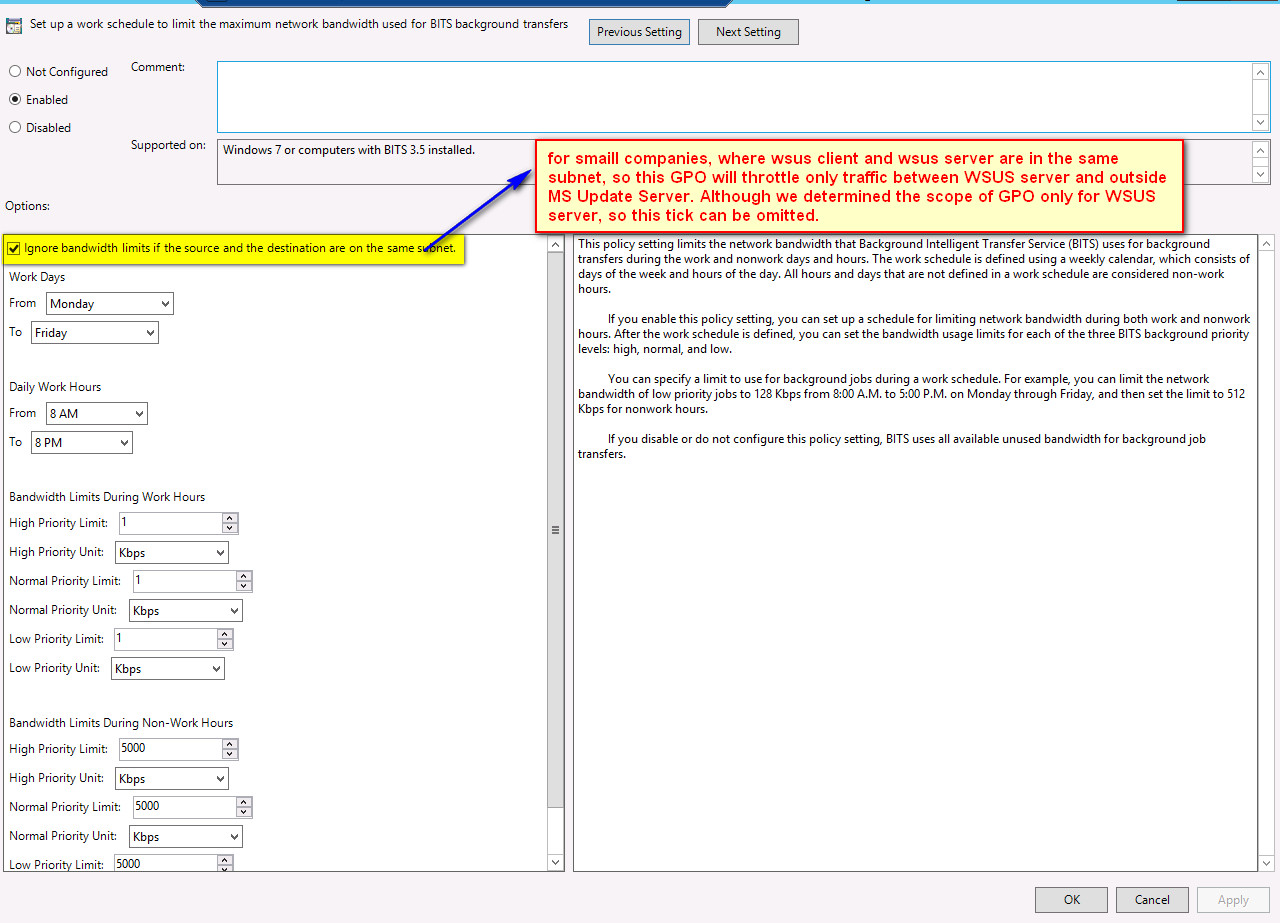
Step2:
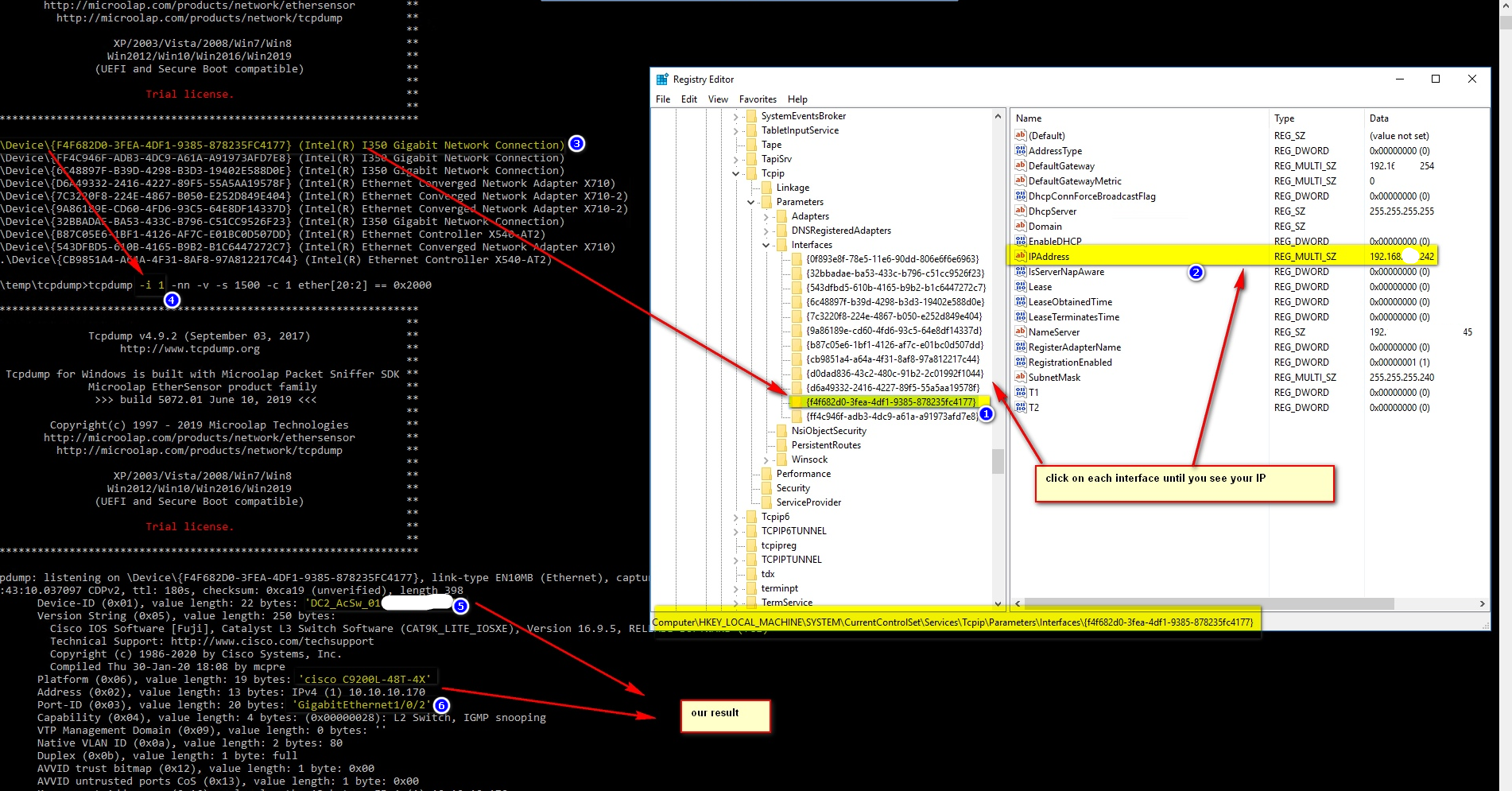
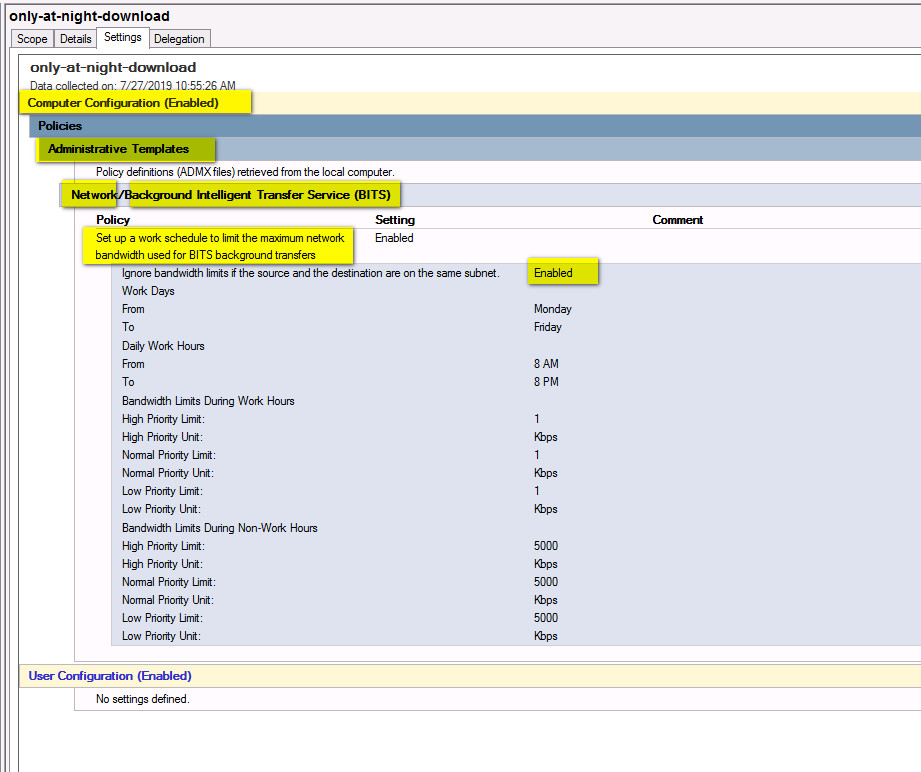
Step3:
Now we know value for parameter -i
c:\temp\tcpdumptcpdump -i 1 -nn -v -s 1500 -c 1 ether[20:2] == 0x2000 ******************************************************************** ** ** ** Tcpdump v4.9.2 (September 03, 2017) ** ** http://www.tcpdump.org ** ** ** ** Tcpdump for Windows is built with Microolap… Read the rest