Coronavirus forced many people, companies to move to teleworking. The banks and large corporations surely have enough budget to buy enterprise vpn boxes and solutions. My post is only for small companies which need free/cheap solution to access own small office infrastructure during coronavirus pandemia from home, remote offices and at the same time to avoid directly openning RDP access from the internet (which is not safe at all even with DUO 2fa and so on)
It’s assumed that the small company has at least
- router which can port forward (even tplink and dlink can do it; if you have more robust and expensive routers with builtin vpn servers then this article is not for you)
- some kind of virtualization (even if there is no servers, it can be hyper-v role on windows10 or virtualbox or vmware workstation) backed up by smartUPS.
- internal LAN subnet is for example 192.168.0.0/24; router LAN interface has 192.168.0.1 and WAN IP is 103.1.1.1
in this scenario:
- we install linux (for examle latest at this time debian10.3 netinstall) as VM (10gb vhd/vmdk and 1gb of vRAM, 1 vcpu for 5-10 planned vpn concurrent users ); with IP as 192.168.0.2/24 and dgw is as 192.168.0.1
- create on the router port forwarding rule – udp 51195 is forwarded to 51195 of 192.168.0.2 (for sure port number is your choice, pls change it)
- apt-get update
- nano /etc/profile.d/new-path.sh (if you don’t do this then following steps of NYR script will fail)
- add into this new script only one line “export PATH=$PATH:/sbin”
- chmod 777 /etc/profile.d/new-path.sh
- source /etc/profile
- reboot
- cd /root
- wget https://git.io/vpn -O openvpn-install.sh && bash openvpn-install.sh
- when asked configure as : 103.1.1.1 ; udp port; 31195;dns – google; yourcompanyname-31195-username
- when NYR script is stopped, i recommend to protect each ovpn file by password (otherwise it can be stolen and used). for this :
- cd /root
- chmod 777 openvpn-install.sh
- nano openvpn-install.sh and change only one line:
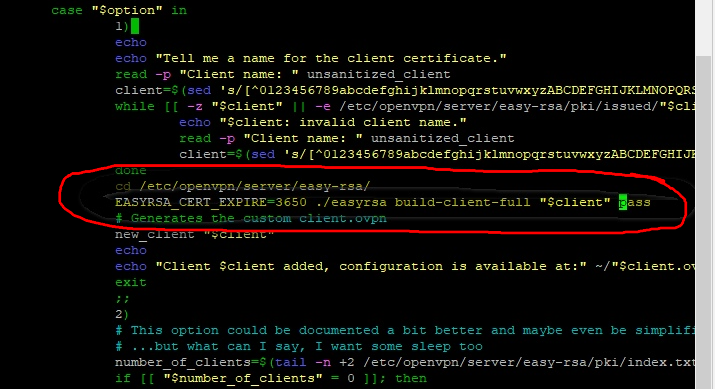
- now if you again run NYR script ./openvpn-install.sh then you will be asked for pem certificate password
- now send by email generated ovpn files (one for each remote worker, don’t send the same file to several users – otherwise they will kick off each other if access simultaneously)
- better to send password separately (for example by sms) and instruct to keep password in safe (the end user can in the openvpn client save password it’s ok)
- instruct each teleworker to download and install openvpn client
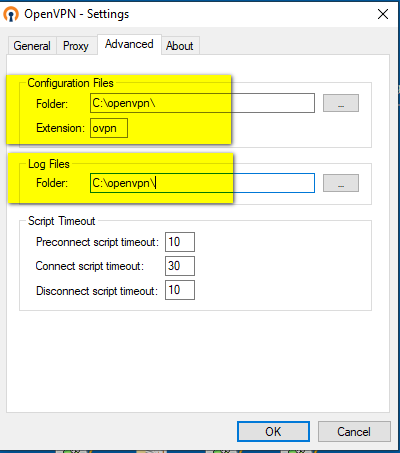
- create in windows c:\openvpn folder
- place ovpn file inside c:\openvpn
- and configure openvpn client to use this config file:
- that’s all
ps
Here is the error if you don’t follow above instructions
Unable to initialize the iptables/netfilter NAT table, setup can’t continue.
If you are a LowEndSpirit customer, see here: https://git.io/nfLES
If you are getting this message on any other provider, ask them for support.